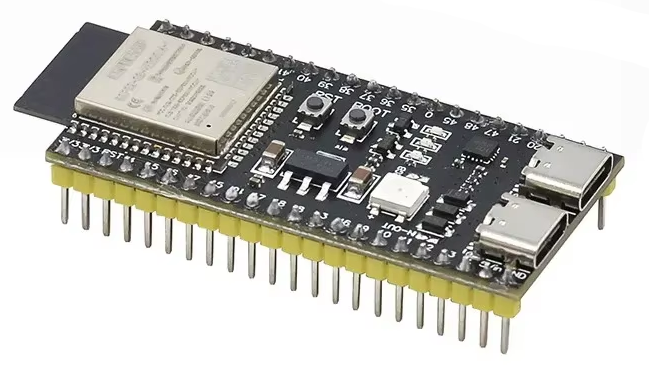
Getting started with the ESP32 microcontroller
The ESP32 is a powerful and versatile microcontroller that’s perfect for DIY electronics projects. I’ve found them a useful addition to my home tech options, particularly due to their small size and low power consumption. If you’re a Raspberry Pi fan (as I am) the ESP32 offers a smaller, lower power option for simple scenarios […]